Does RecoveryManager Plus support TLS v1.2 protocol?
Yes, RecoveryManager Plus supports TLS v1.2. The product can be configured to use only this protocol by following the steps mentioned below. Before you proceed, please enable SSL and apply an SSL certificate in RecoveryManager Plus as explained in this document.
Steps to make RecoveryManager Plus to use only TLS v1.2
RecoveryManager Plus can be configured to use PostgreSQL and MS SQL databses. The steps to enable RecoveryManager Plus to only use TLS v1.2 will vary depending on the database used.
For PostgreSQL database
- Stop RecoveryManager Plus.
- Navigate to <installation_dir>/conf/ where <installation_dir>/ is the location where RecoveryManager Plus is installed and open the server.xml file.
- Change the Value of sslEnabledProtocols in Connector tag to TLSv1.2.
- In /conf/wrapper.conf, modify:
wrapper.java.additional.xx=-Dhttps.protocols=TLSv1,TLSv1.1,TLSv1.2 to wrapper.java.additional.xx=-Dhttps.protocols=TLSv1.2
Note: xx can be any integer; do not change it.
- Copy the information mentioned below and paste after acceptCount="100" in Connector SSLEnabled
ciphers="TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,
TLS_RSA_WITH_AES_128_CBC_SHA256,
TLS_RSA_WITH_AES_128_CBC_SHA,
TLS_RSA_WITH_AES_256_CBC_SHA256,
TLS_RSA_WITH_AES_256_CBC_SHA"
- Restart RecoveryManager Plus.
For MS SQL database
Before you proceed, check if the current installation of MS SQL Server supports TLS v1.2. If not, update your database with the service pack from here.
- Stop RecoveryManager Plus.
- Configure the logon credentials for SQL Server service with the admin account.
- Generate a certificate using IIS Manager, by following the steps listed below.
- Open IIS Manager in the Server where MS SQL is installed (type 'inetmgr' in the Run window).
- Select Server Certificates.
- Select Create Self-Signed Certificate on the Actions window.
- Provide a Friendly Name for the Certificate, and let the Certificate Store be Personal"strong.
- Once done, the certificate will be installed in Personal Certificate Store and will be available in the SQL Server Configuration Manager for Certificate Association.
- Associate the certificate with your SQL Server.
Note: To associate an SSL certificate to MS SQL server, the certificate should have been imported to Personal Certificate Store.
To import the certificate to Personal Certificate Store,
- If Self Signed Certificate is created through IIS, then it is automatically imported. If not, it should be imported using the following steps.
- Open IIS Manager(Run command: inetmgr).
- Select Server Certificates.
- Select import from the Actions window.
- Browse the *.pfx file generated(Certificate should have been associated with private key) generated.
- Open SQL Server Configuration Manager.
- Select SQL Server Network Configuration.
- Right click on Protocols and select Properties for the instance that you want to associate the certificate.
- In the Flags tab, select Force Encryption to YES.
- In the Certificate Tab, select the certificate using the drop down.
- Changes will be reflected, only when the Service is restarted. So restart the SQL Server service.
- Navigate to <installation_dir>/conf/. In the database_params.conf file, change url=jdbc:jtds:sqlserver://<server-name>:1434/DB6653_2;ssl=request to url=jdbc:jtds:sqlserver://<server-name>:1434/DB6653_2;ssl=require/authenticate
- Navigate to <installation_dir>/conf/ and open the wrapper.conf file.
- Navigate to <installation_dir>/conf/ and open the server.xml file.
- In the Connector tag, remove TLSv1 and TLSv1.1 from sslEnabledProtocols, leaving only TLSv1.2 in the value.
- Copy the information mentioned below and paste after acceptCount="100" in Connector SSLEnabled
ciphers="TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,
TLS_RSA_WITH_AES_128_CBC_SHA256,
TLS_RSA_WITH_AES_128_CBC_SHA,
TLS_RSA_WITH_AES_256_CBC_SHA256,
TLS_RSA_WITH_AES_256_CBC_SHA"
- Replace jtds-1.3.1.jar
- Download the JAR from this link. Replace the downloaded JAR file in the <installation_dir>/lib folder.
- Start RecoveryManager Plus.
If you need further assistance or information, please get in touch with us at support@recoverymanagerplus.com
Steps to disable older TLS versions in Elasticsearch
- Navigate to <installation>\ES\config.
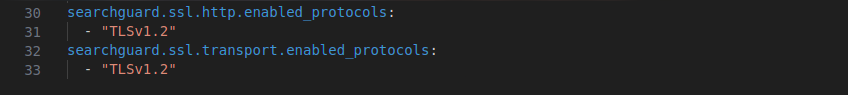
- Open elasticsearch.yml file and add the below lines at the end of the file.
searchguard.ssl.http.enabled_protocols:
- "TLSv1.2"
searchguard.ssl.transport.enabled_protocols:
- "TLSv1.2"
- Save the file and restart RecoveryManager Plus for the changes to take effect.