 ×
×Direct Inward Dialing: +1 408 916 9892
Get a clear picture of all the changes made to your AD resources with ManageEngine ADAudit Plus. Strengthen your security posture and quickly detect and respond to insider threats, privilege abuse, and other indicators of compromise.
Get your free trial fully functional 30-day trial
Generate a cumulative report on Active Directory changes across all configured entities.
Selectively monitor AD changes made by specific users or a group of users for in-depth analysis.
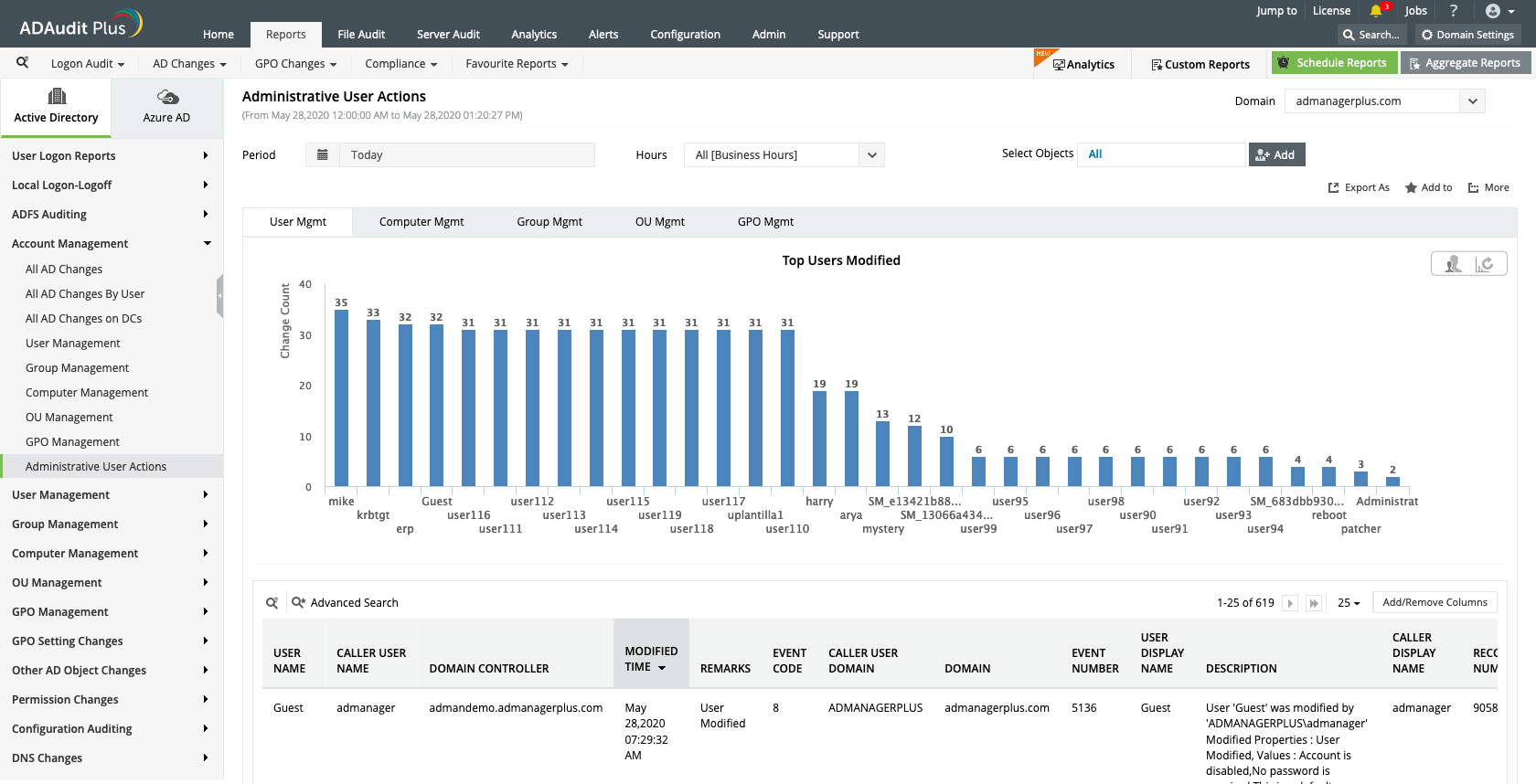
Get the big picture:Generate a cumulative report on Active Directory changes across all configured entities.
Drill down deeper:Selectively monitor AD changes made by specific users or a group of users for in-depth analysis.
Keep track of users with the most failed authentication attempts to prevent security threats.
Quickly track the number of users currently logged in with details on who logged in from where.
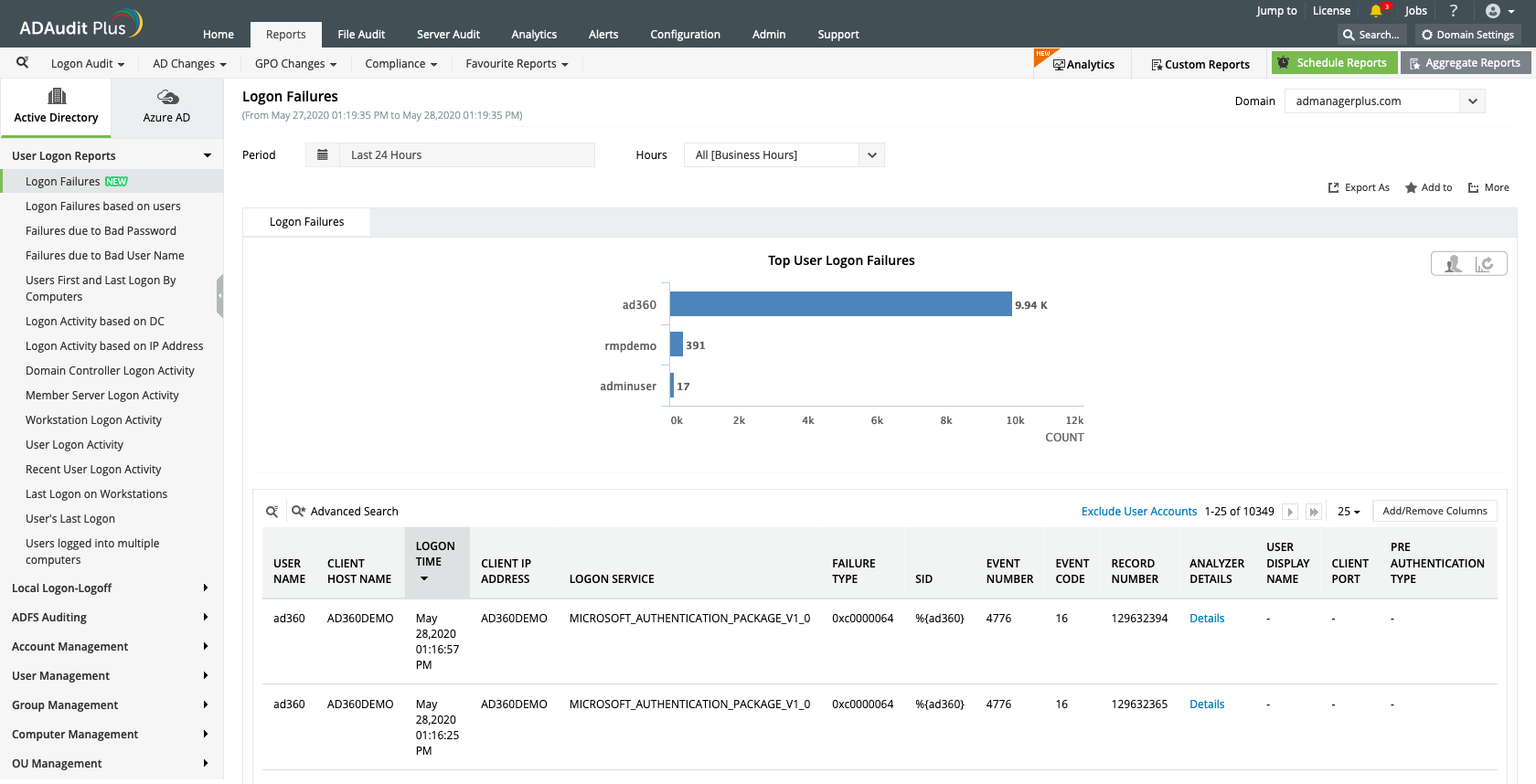
See what's happening:Quickly track the number of users currently logged in with details on who logged in from where.
Perform failure analysis:Keep track of users with the most failed authentication attempts to prevent security threats.
Keep track of recently locked-out user accounts and view relevant details for further analysis.
Identify the source of the most repeated account lockouts by checking multiple Windows components.
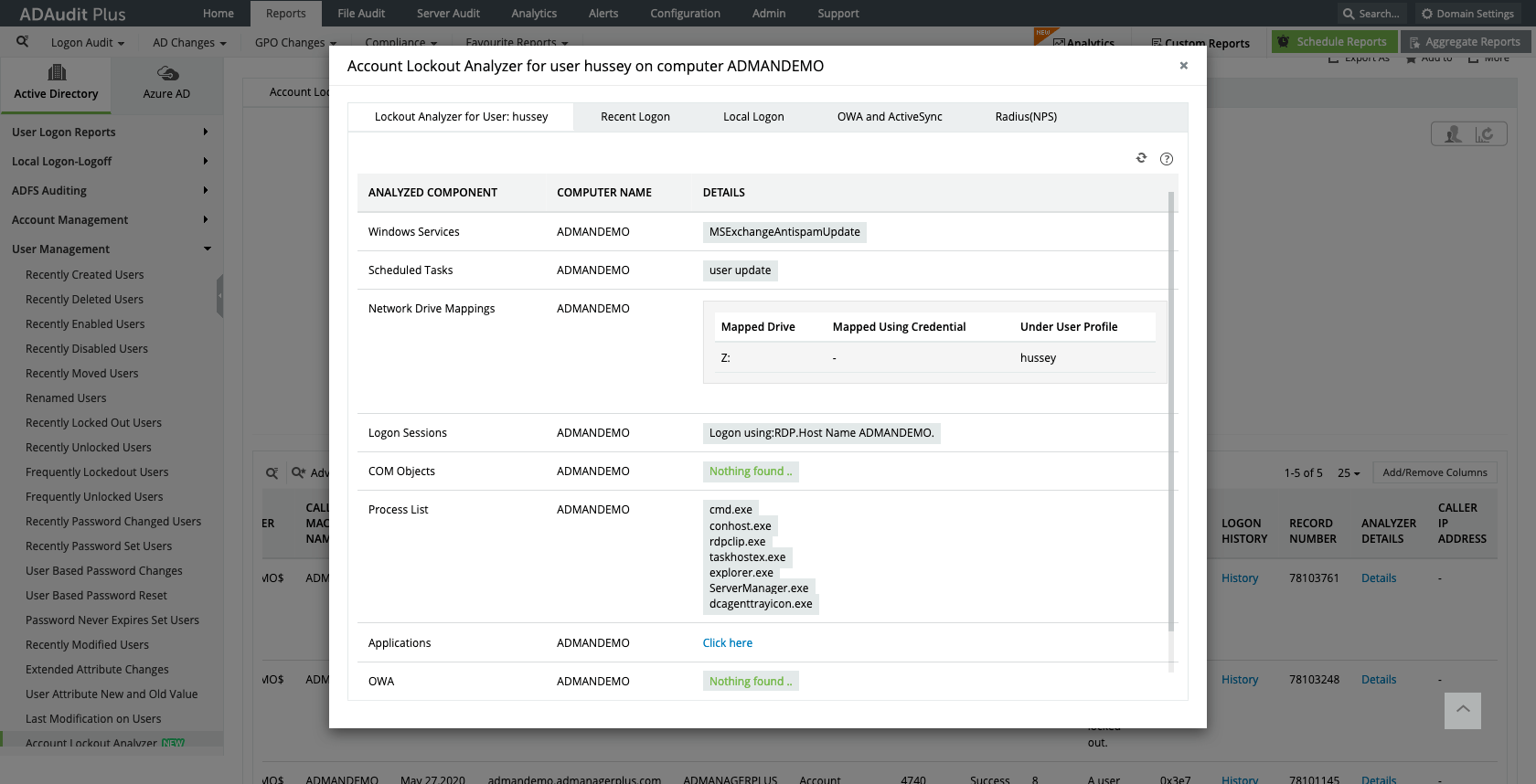
Find the most recent data: Keep track of recently locked-out user accounts and view relevant details for further analysis.
Analyze and troubleshoot: Identify the source of the most repeated account lockouts by checking multiple Windows components.
Use the multiple predefined report categories available to track different types of GPO setting changes for in-depth analysis.
Quickly identify the old and new values of a modified GPO, and view information about who modified it and when.
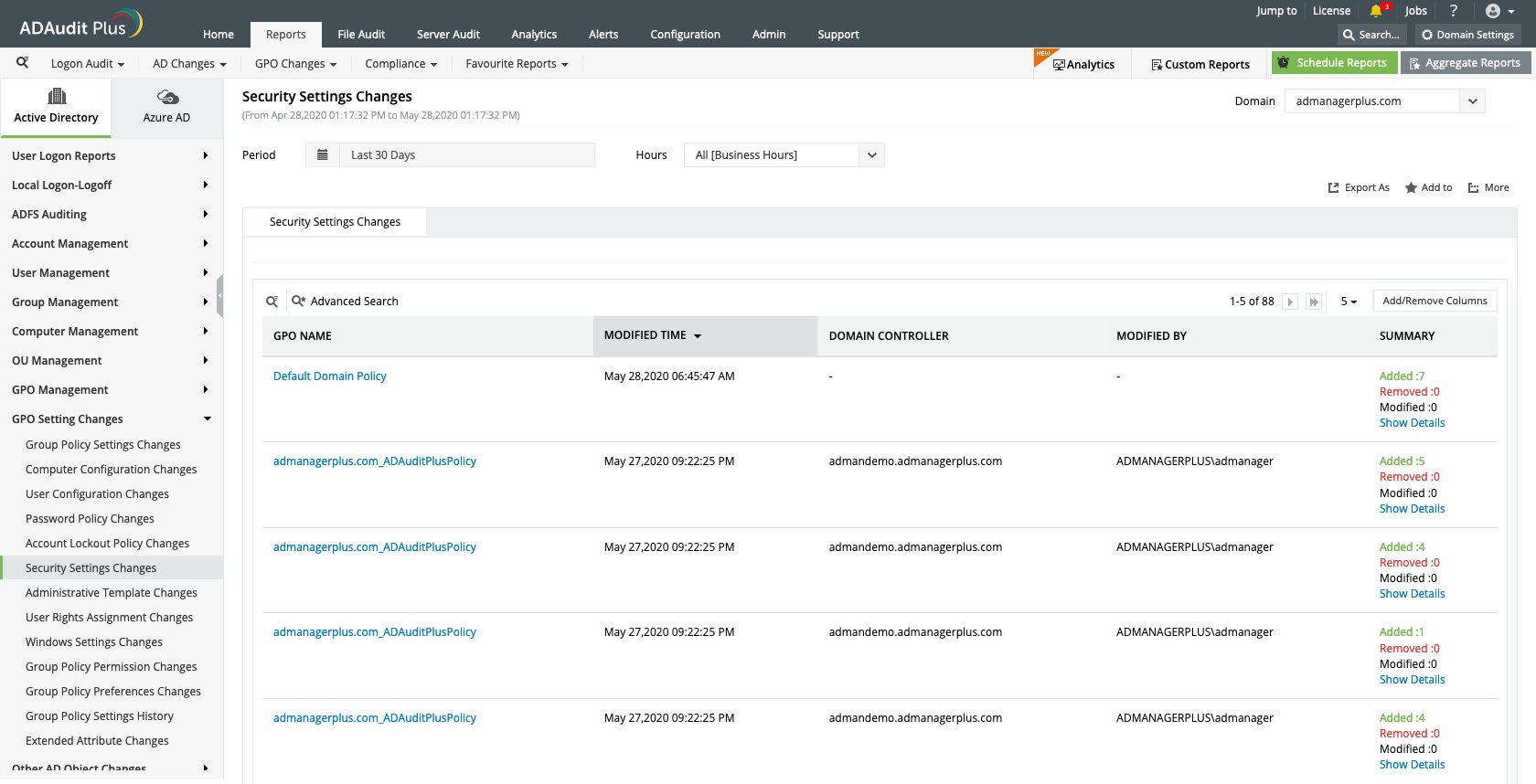
Get granular: Use the multiple predefined report categories available to track different types of GPO setting changes for in-depth analysis.
Gain contextual information: Quickly identify the old and new values of a modified GPO, and view information about who modified it and when.
Detect anomalies across various types of user activities, including logins, using machine learning.
Analyze the particulars for each and every unusual activity that’s detected.
Browse through the baseline, or typical behavior, of every user in your organization.
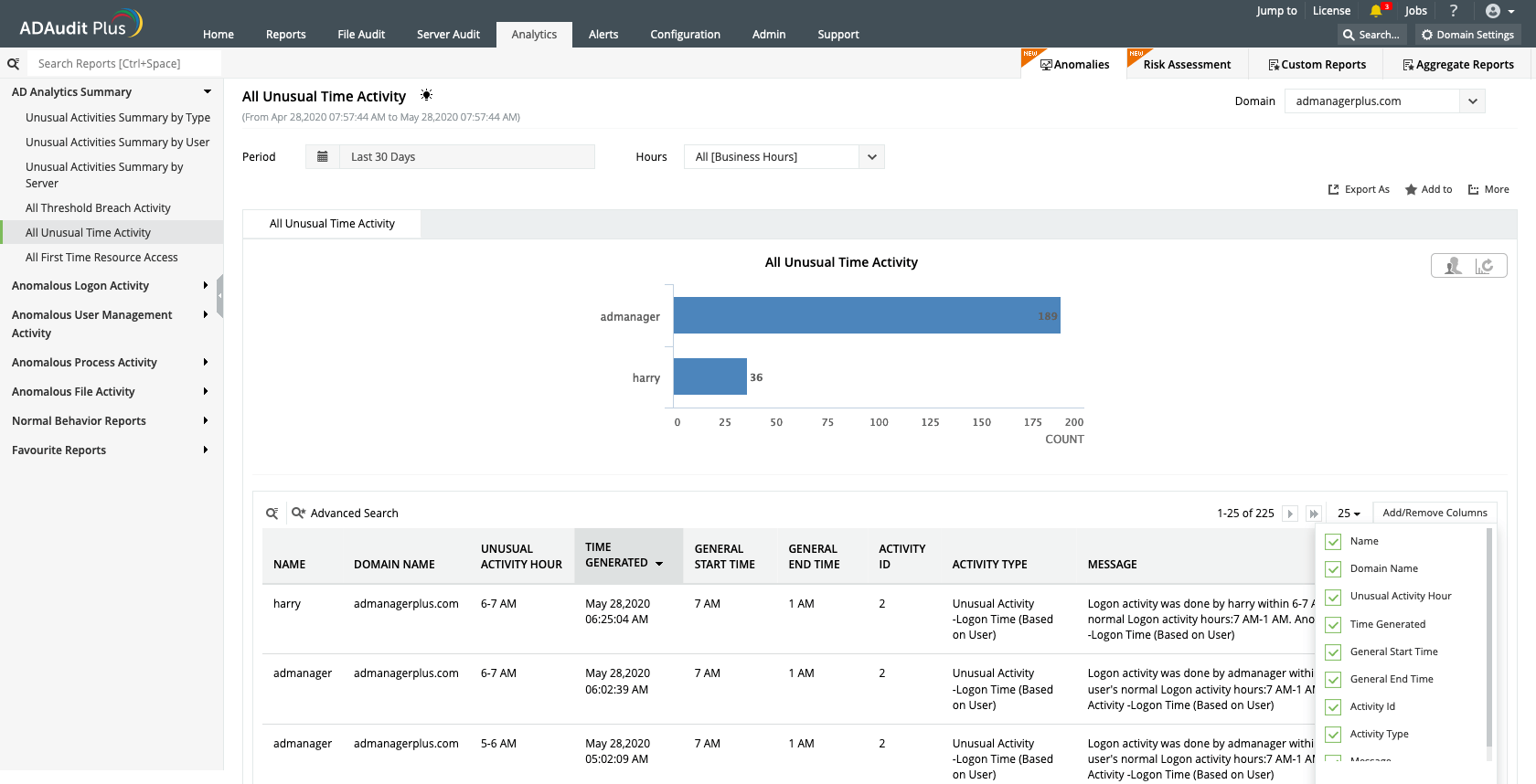
Simplify anomaly detection: Detect anomalies across various types of user activities, including logins, using machine learning.
Learn the specifics: Analyze the particulars for each and every unusual activity that’s detected.
Know what's normal: Browse through the baseline, or typical behavior, of every user in your organization.
Get a bird's eye view of your AD's security profile with the exclusive AD threat dashboard and keep an eye out for any indicators of compromise.
Detect and mitigate over 25 common AD attacks with dedicated threat reports.
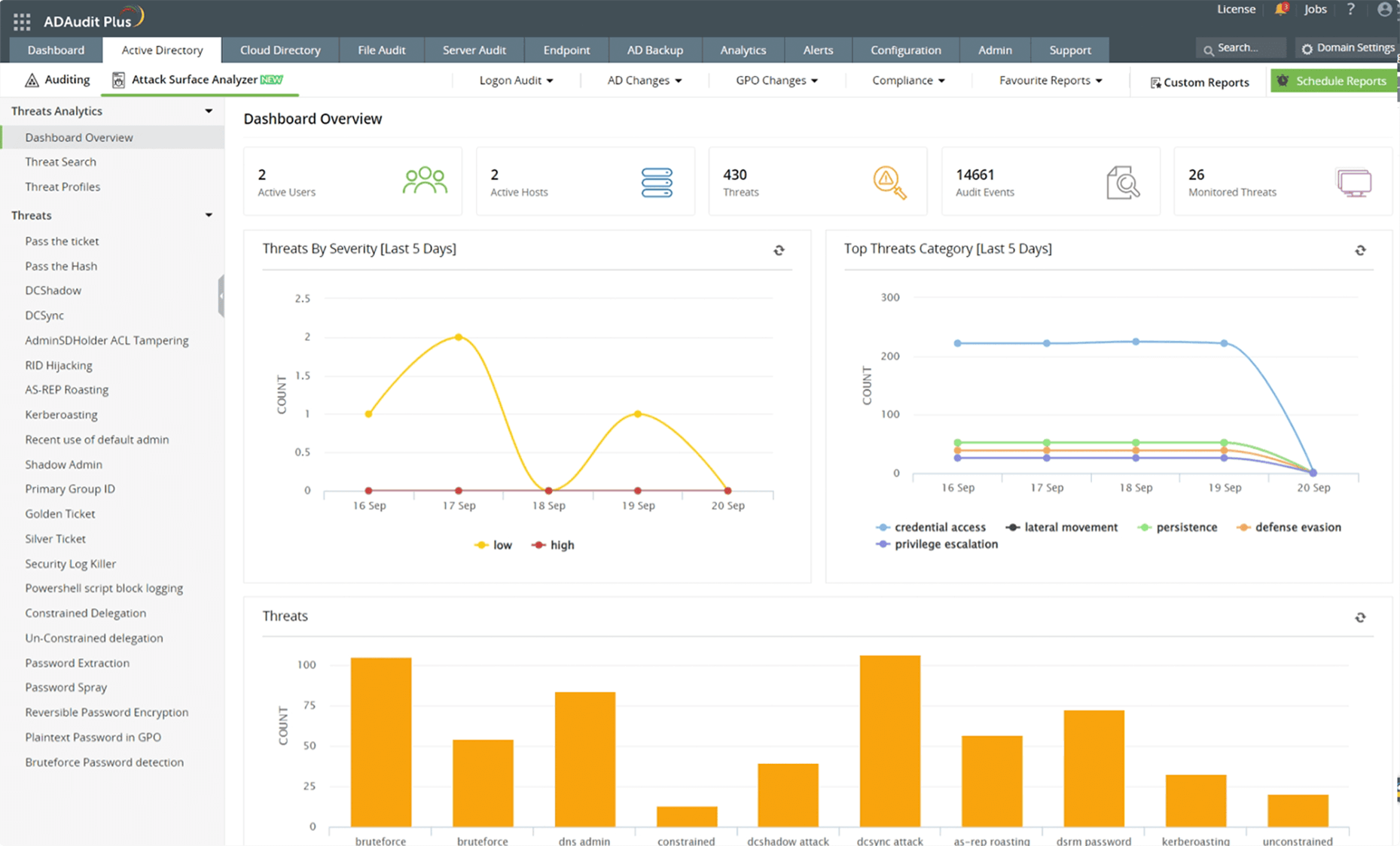
Secure your AD : Get a bird's eye view of your AD's security profile with the exclusive AD threat dashboard and keep an eye out for any indicators of compromise.
Thank you for your interest in ManageEngine ADAudit Plus. We have received your request for a price quote and will contact you shortly.
Our Active Directory auditing software offers extensive out-of-the-box compliance reports that helps streamline and meet multiple compliance requirements.
Track accesses and modifications to shares, files, and folders in your Windows file server environment.
Track file changes across Windows, NetApp, EMC, Synology, Hitachi, Huawei, Amazon FSx for Windows, QNAP, and Azure file servers.
Perform change monitoring on all activities across the Windows server environment in real-time.
ADAudit Plus is a UBA-driven change auditing solution that helps ensure accountability, security, and compliance across your Active Directory (AD), file servers, Windows servers, and workstations.