Data encryption must be highly prioritized in an enterprise network. For businesses with vast number of machines, it will be difficult to manually enable BitLocker. This is where the BitLocker module in Endpoint Central serves as a solution to manage and secure your drives.
Create policies for BitLocker drive encryption for machines within your network to secure your data. The BitLocker module in Endpoint Central enables you to build flexible policies to encrypt your drives according to your machine's requirement.
NOTE - Adhere to BitLocker encryption pre-requisites before deploying an encryption policy.
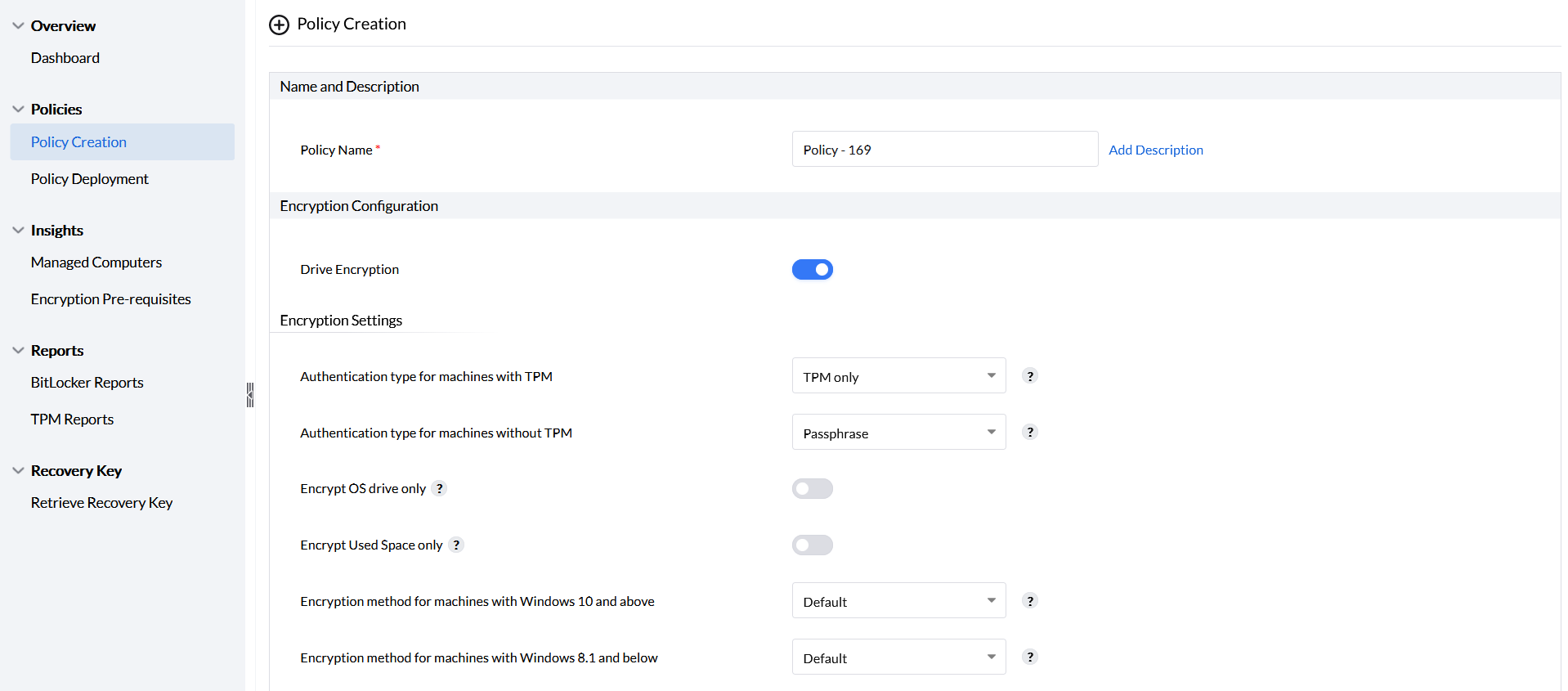
when this setting is enabled, the drives will be encrypted
Once the setting is enabled, the BitLocker policies allow you to access and choose encryption settings for machines within your network.
The BitLocker policies help you to secure your machines with authentication. The authentication type varies for machines with TPM and for machines without TPM.
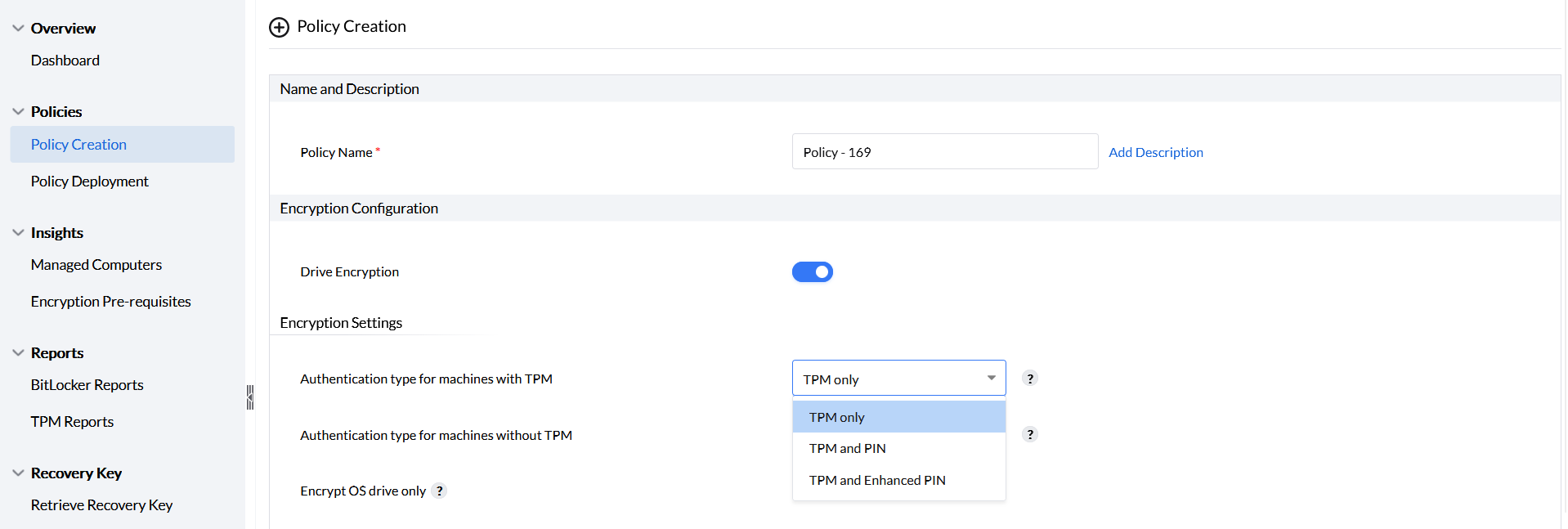
Authentication for machines with TPM can be enabled by choosing any of the three options provided as shown in the image.
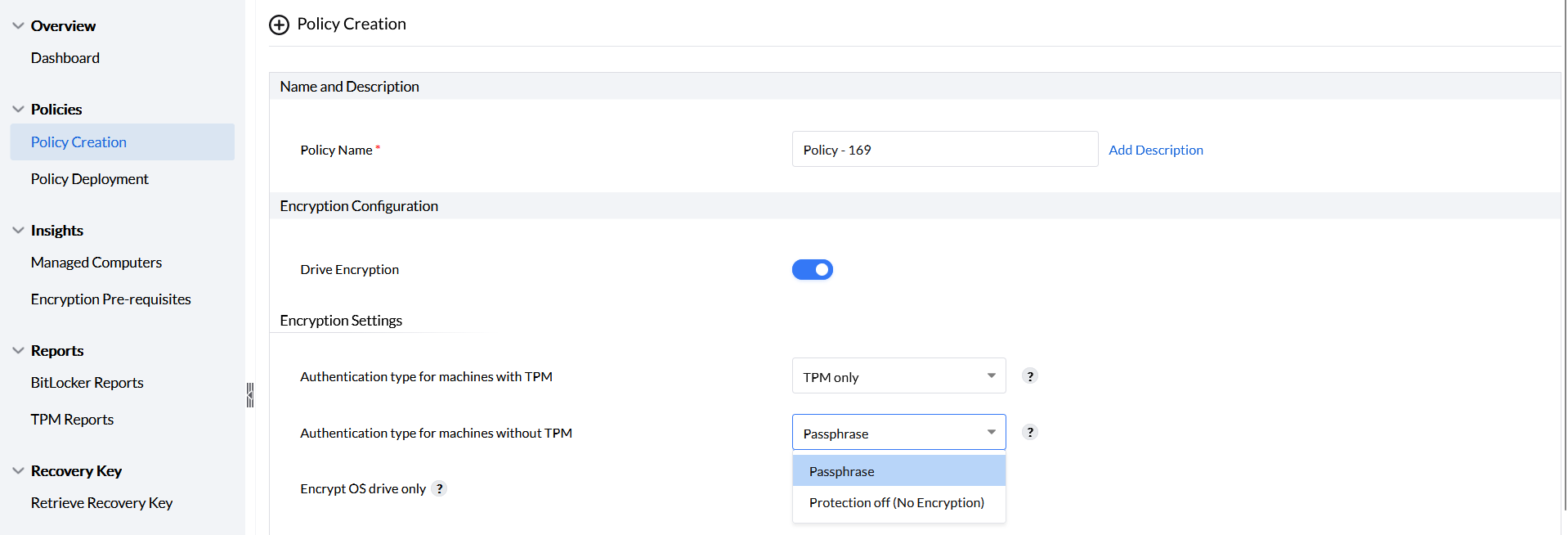
Authentication for machines without TPM can only be enabled with the passphrase option. This will prompt the user to enter a passphrase every time the computer is started.
Encryption of your drives can be optimized with the encryption settings provided by the BitLocker policies. You are provided with three encryption policies where you can apply policies by combining them if required.
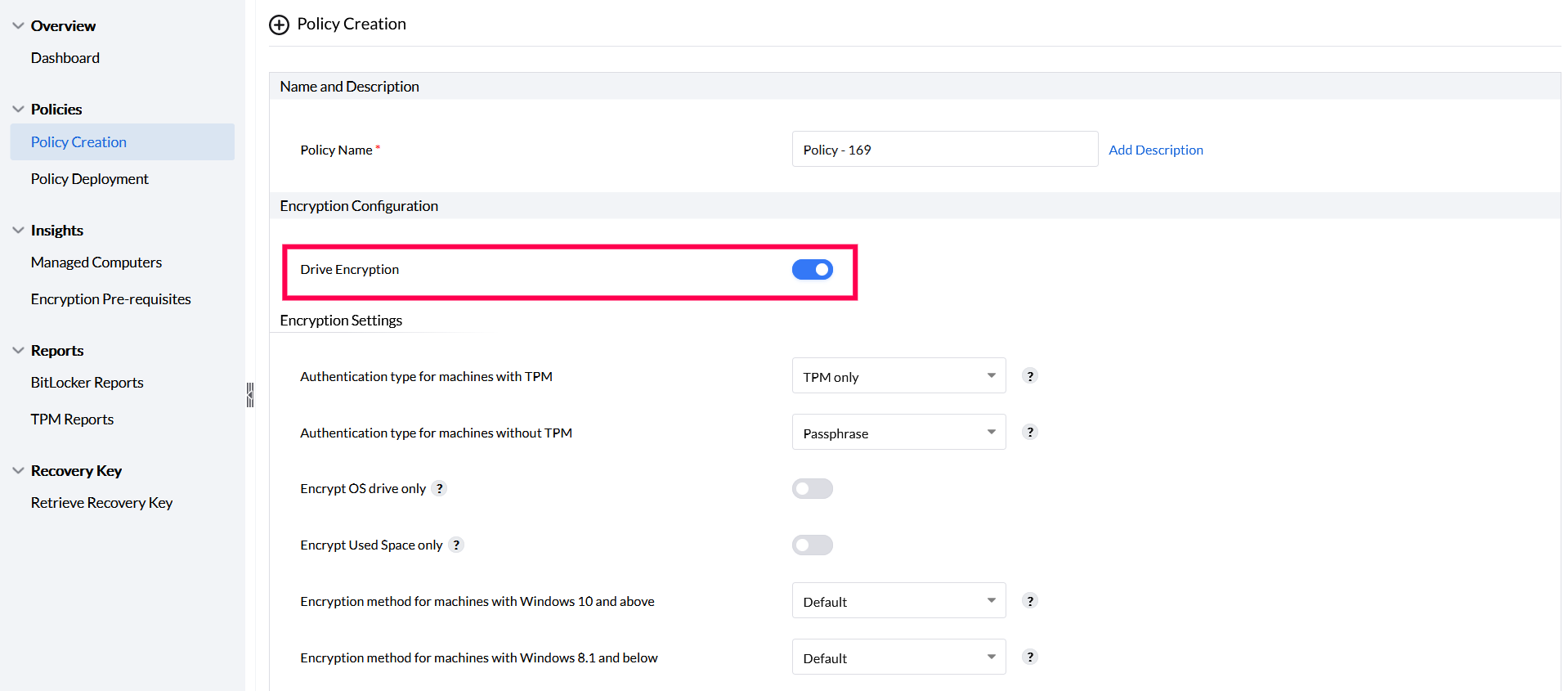
For full space encryption, enable only the Drive Encryption setting.
To encrypt only the OS drive, enable the option Encrypt OS drive only in the Encryption Settings section.
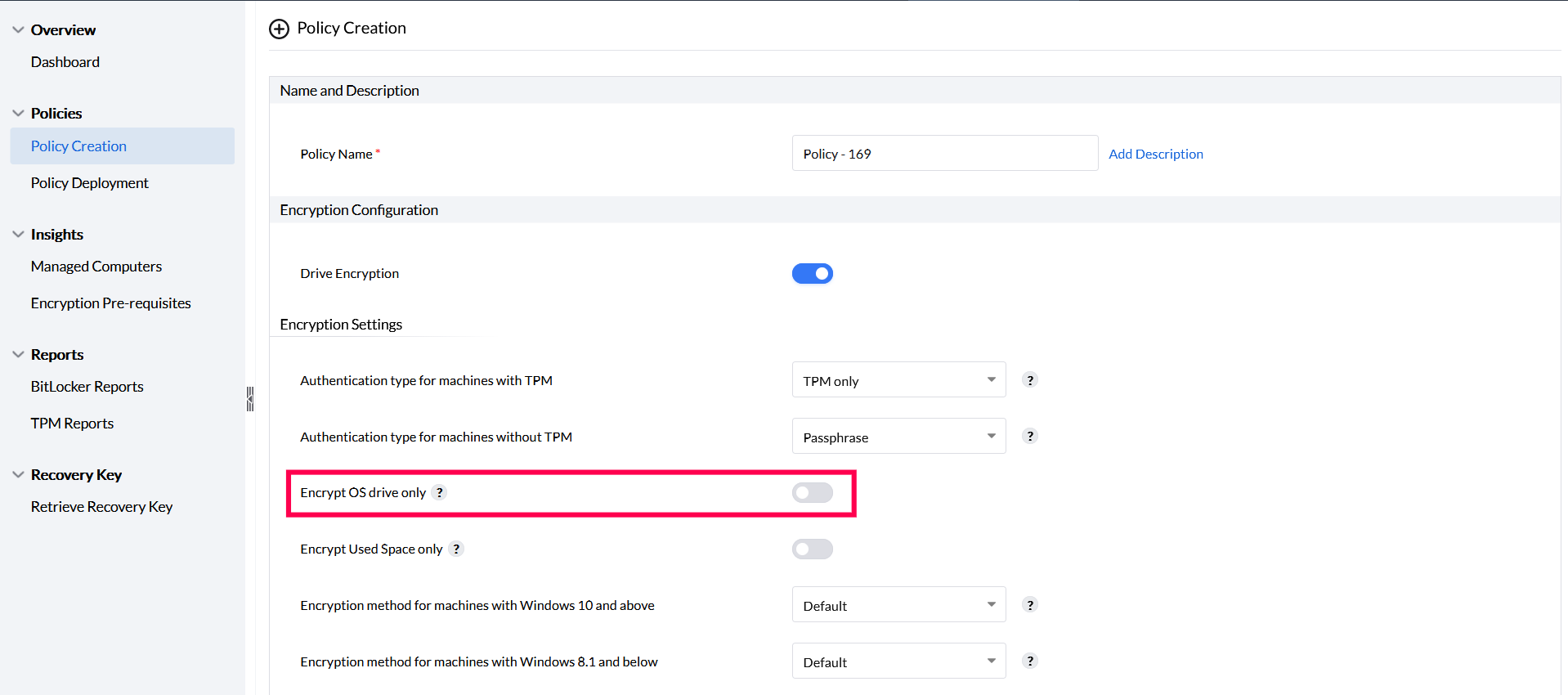
This will ensure that all volumes in the OS drive are encrypted and that all other data drives will be or remain decrypted.
To encrypt only the used space, enable the option Encrypt used space only in the encryption settings section.
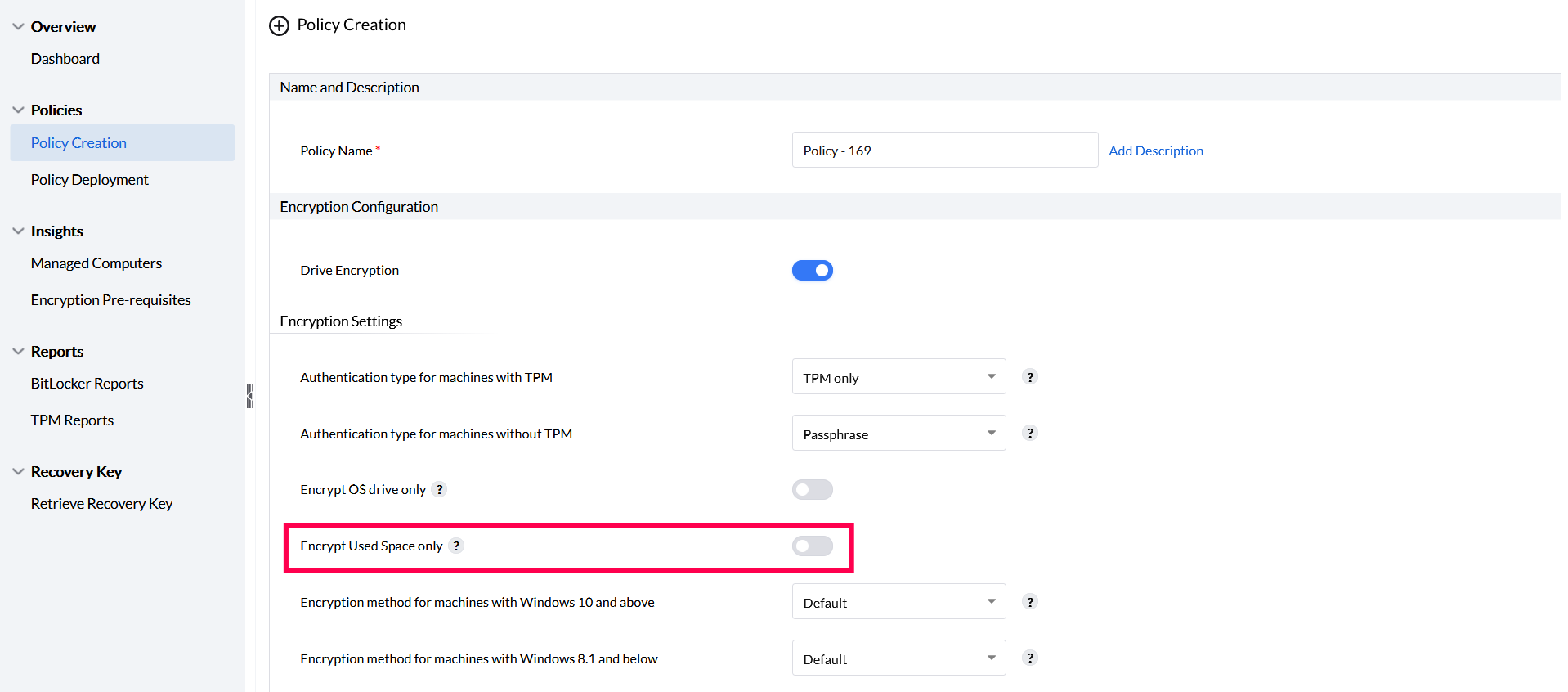
This ensures encryption of only the used space in your drives while the free space available on your drives will be or remain decrypted.
BitLocker gives you additional settings on how to encrypt your machines with different encryption methods. There is a specific set of encryption methods that are available for machines with Windows 10 & above and for machines with Windows 8.1 & below. The default method would be either the method previously configured using GPO or the encryption method already associated with your system OS
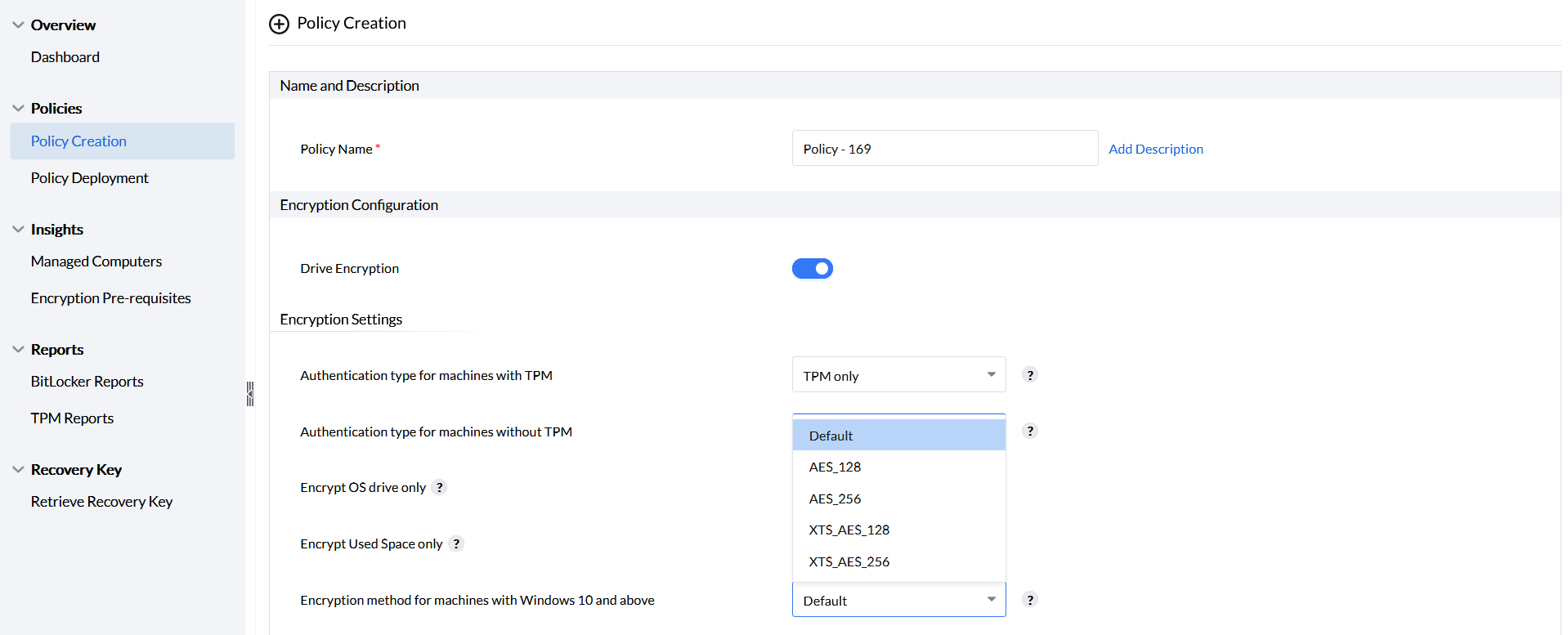
The encryption methods available in this drop down are applicable.
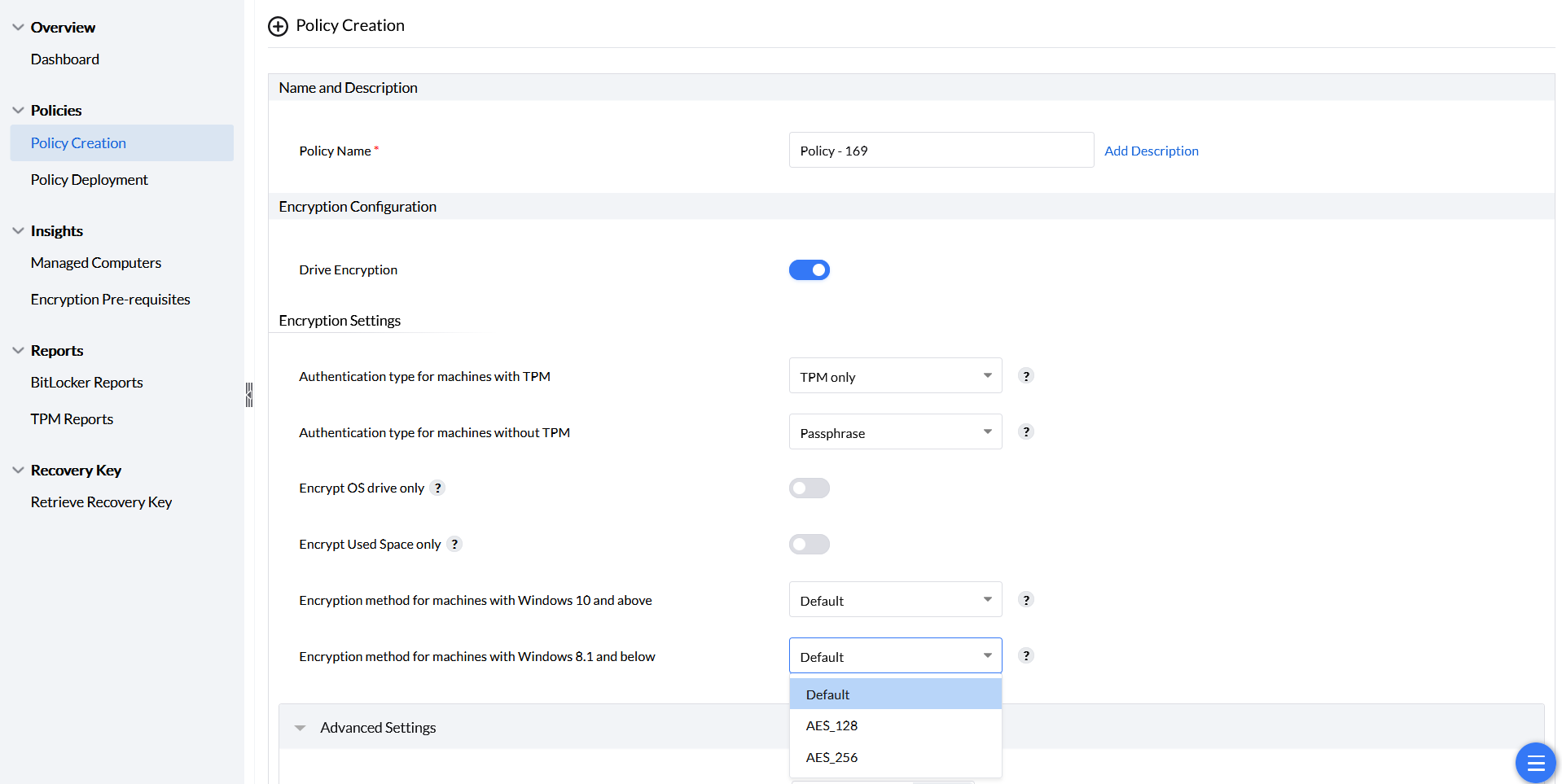
The encryption methods available in this drop down are applicable.
The BitLocker policies contain advanced settings where you can postpone restart, configure recovery key update and rotation period.
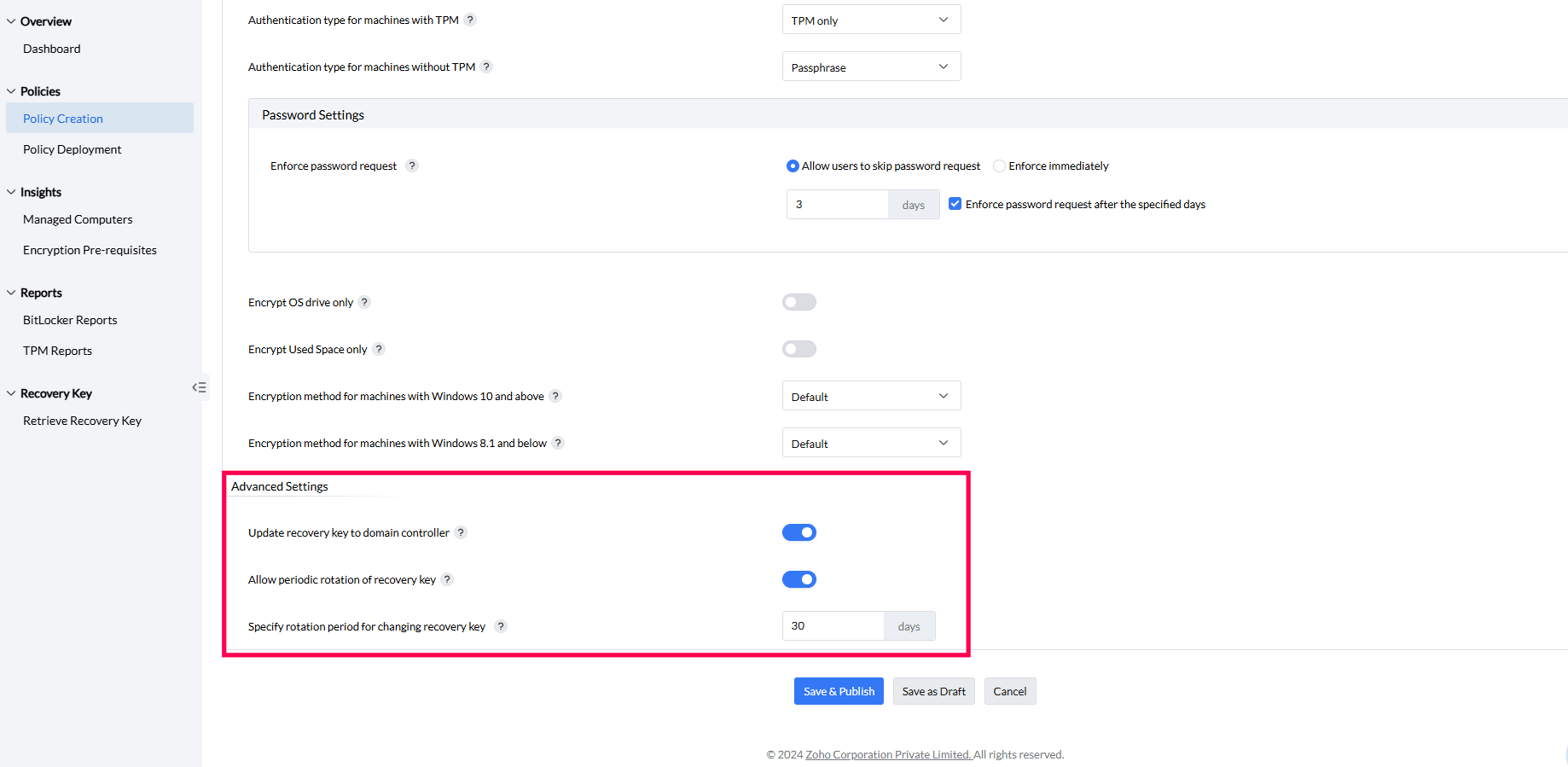
Once the above mentioned settings have been configured according to your requirements, you can save as a draft or save and publish directly.
Once a policy has been created and saved. It will be available in the policy list in the Policy Creation view.
You have successfully created an encryption policy.
The BitLocker add-on also enables you to decrypt the drives based on your requirement.
When the setting is disabled, all the drives will be decrypted.
You can now save and publish directly.
Once a policy has been created and saved. It will be available in the policy list in the Policy Creation view.
You have successfully created a decryption policy.
Download a 30-day free trial and try it out for yourself!
For more information on the new Endpoint Security suite products including BitLocker Management, refer here.