1. What is HIPAA?
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a federal law designed to refine the movement and continuity of health insurance coverage in individual and group markets.
Title I of HIPAA compliance: HIPAA ensures health insurance coverage for employees and their families when there is a shift in or loss of jobs.
Title II of HIPAA compliance: Also known as the the Administrative Simplification (AS) provisions, this section encourages the electronic exchange of healthcare information. These provisions outline the standards and policies for protecting personally identifiable information maintained by healthcare bodies. They also require the establishment of standards for electronic healthcare transactions and national identifiers for providers, health insurance plans, and employers.
The Omnibus Rule: The Omnibus Rule defines privacy and security requirements for healthcare providers, health plans, and other entities that process health insurance claims. It encompasses requirements for business associates of these entities that hold access to protected health information.
2. What comes under protected health information?
HIPAA is designed to secure the protected health information of patients. This includes all individually identifiable health details like test results, medical history, insurance details, demographic data, and other details specific to a patient and their healthcare services.
3. How does EventLog Analyzer assist companies in meeting HIPAA requirements?
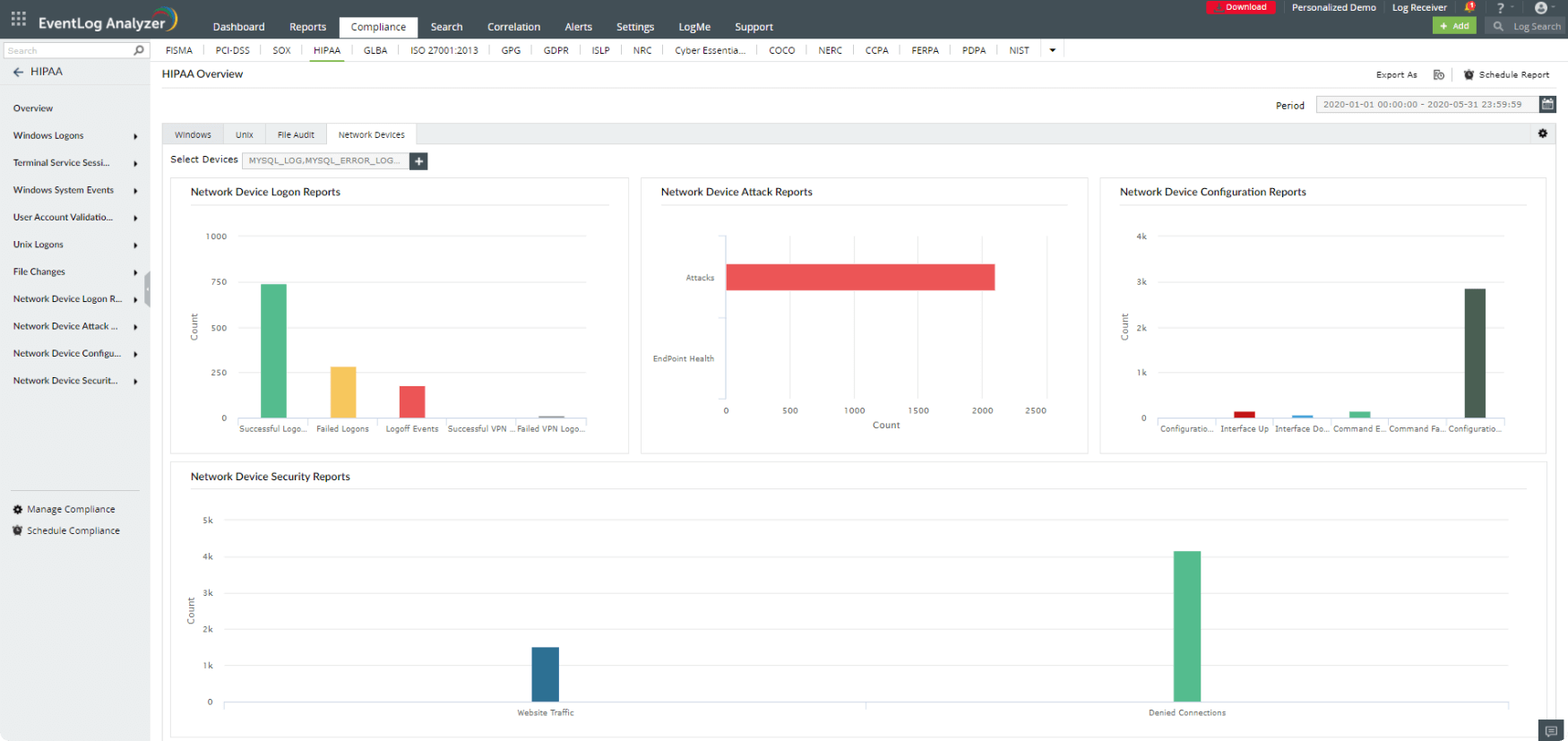
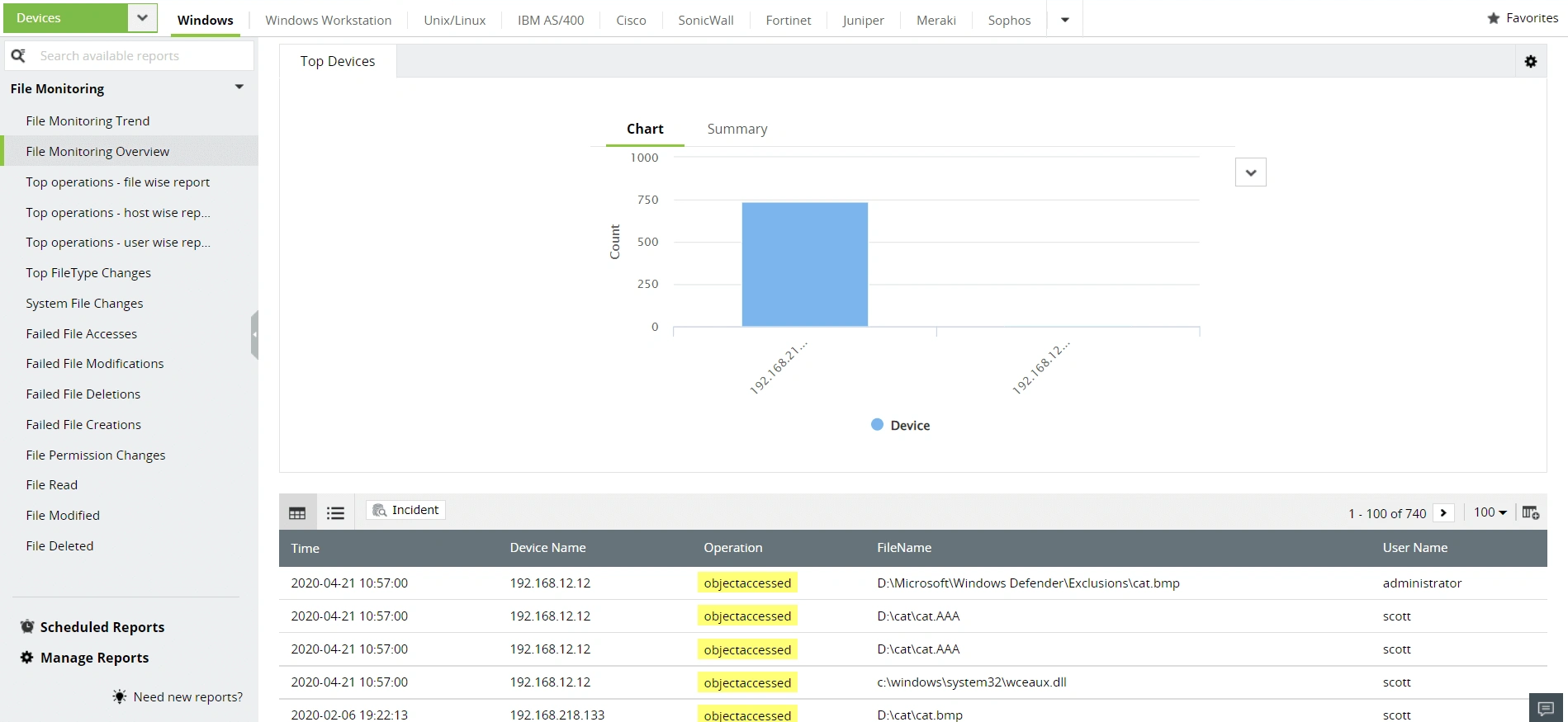
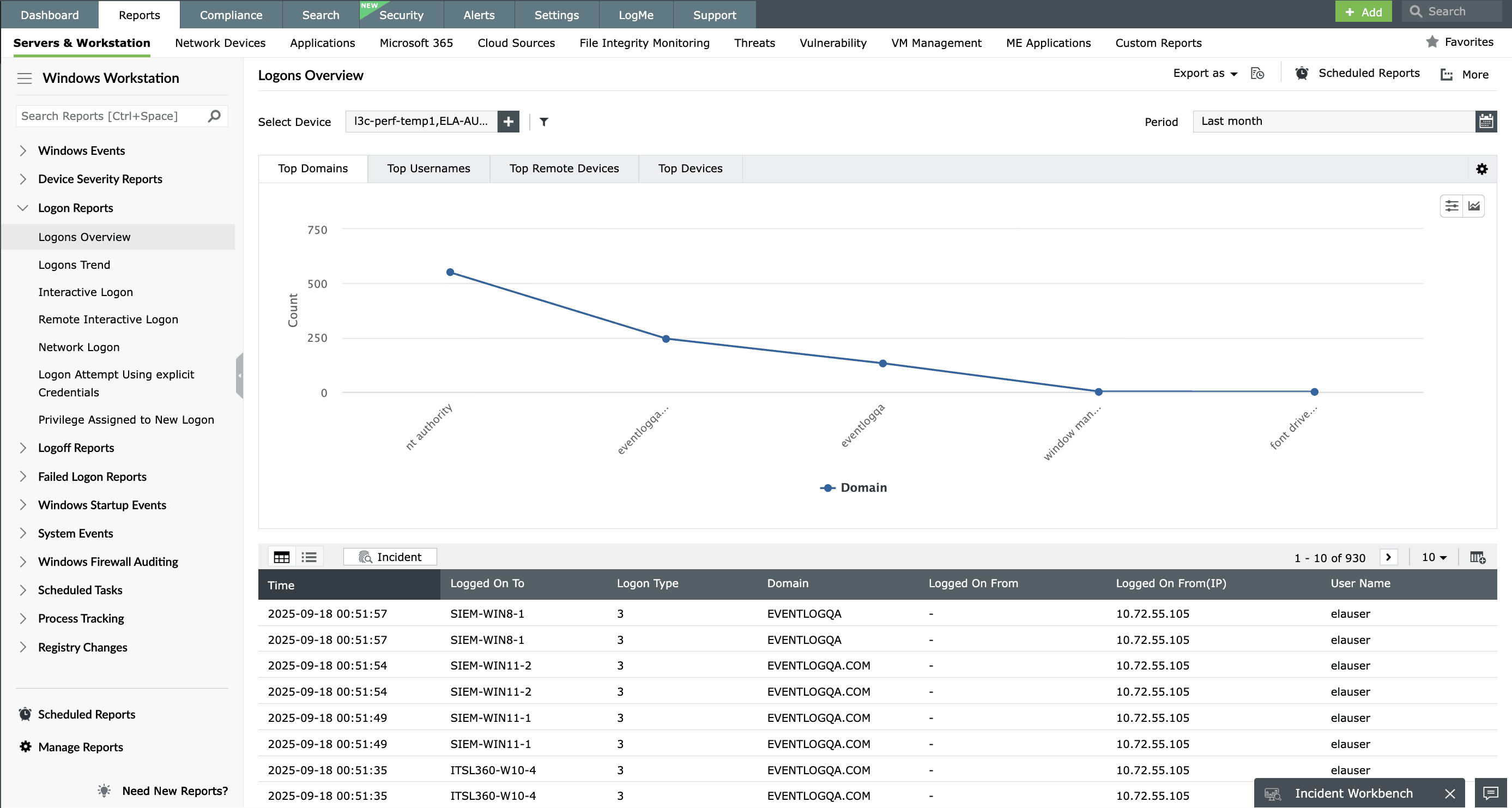
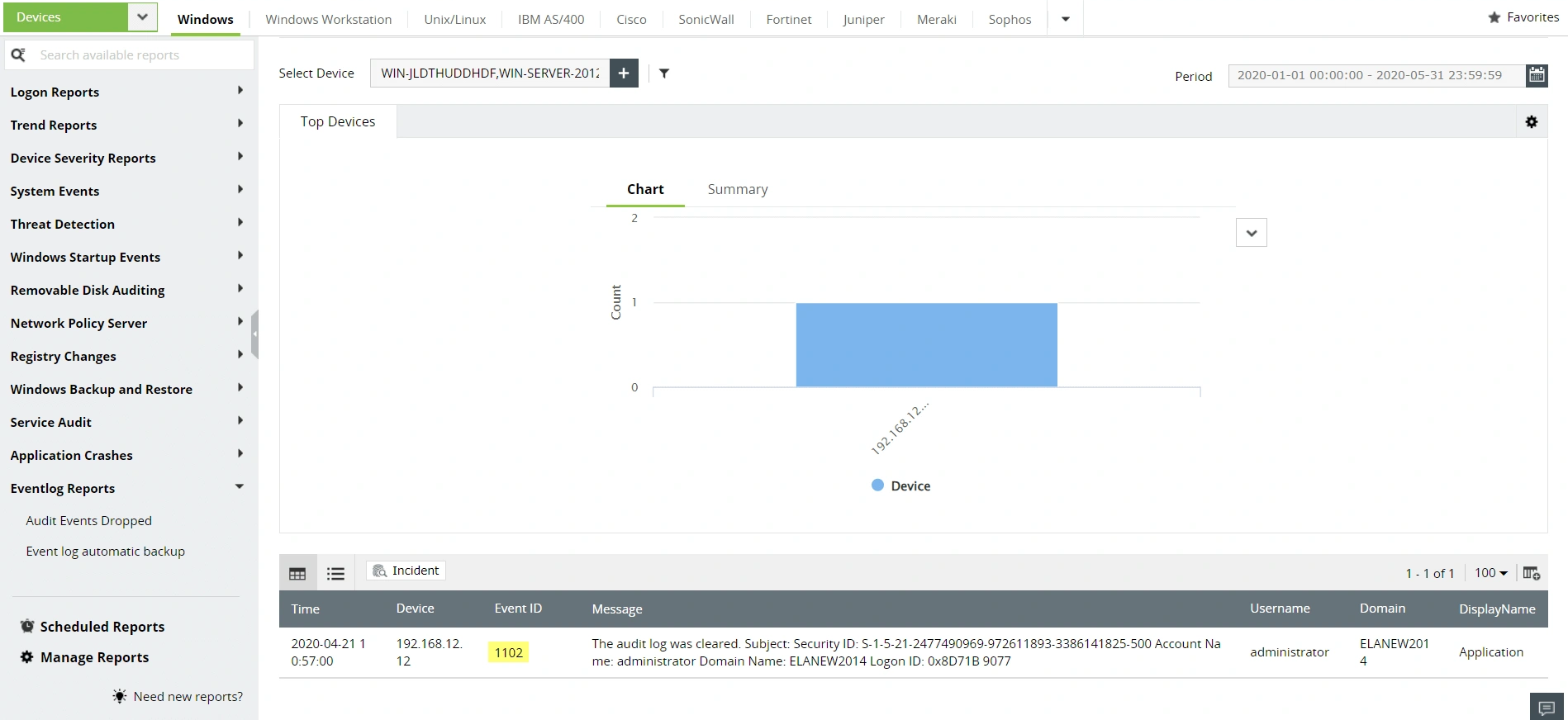
EventLog Analyzer is a unified log management solution that automates log collection and parsing, analyzing, correlating, and archiving your network's log data. The solution makes sense of the network activities and presents them in the form of intuitive dashboards and reports. EventLog Analyzer's in-depth auditing capabilities address IT compliance mandates like HIPAA by monitoring sensitive object access, user account behavior, logon and logoff events, and more. You can also receive instant alerts when any compliance violation is identified in the network. The exhaustive reports provided by the solution simplify compliance management.
EventLog Analyzer supports other common compliance mandates as well.
4. What are the three main rules of HIPAA?
There are three key rules that form the core of HIPAA:
- The privacy rule: It protects the privacy of individually identifiable health information, balancing patient confidentiality with the need to protect public health.
- The security rule: HIPPA sets forth standards for safeguarding electronic PHI (ePHI). It mandates that covered entities enforce extensive administrative, physical, and technical measures to ensure the security of ePHI.
- The breach notification rule: In situations where there is a breach of unsecured PHI, covered entities along with their business associates are bound to notify the affected individuals, the secretary of health and human services, and in certain circumstances, inform the media.
To read more about this, please read our HIPAA compliance guide.
5. What is protected by HIPAA?
HIPAA safeguards all personally identifiable health information held or exchanged by a covered entity or their business associate, regardless of the format — electronic, on paper, or spoken. This protection covers:
- A person's health history, including their past, current, or future physical or mental health condition.
- The provision, or payment for, healthcare services to the individual.
- Any piece of information that could identify an individual or might reasonably be used for identification purposes.
HIPAA ensures PHI is treated with the utmost confidentiality and security. It safeguards patients' privacy rights while enabling the essential flow of health information necessary to ensure high-quality health care.