Smart Card / PKI / Certificate Authentication
(Feature available only in Enterprise Edition)
Since Password Manager Pro serves as the vault for sensitive passwords, it is essential to have a strong authentication mechanism to grant access to the software. Password Manager Pro provides various authentication options and users can choose the ones that suit their environment better. Apart from Password Manager Pro's local authentication, there is provision for leveraging the authentication of external identity stores such as Active Directory / LDAP.
To bolster the security further, Password Manager Pro offers Smart Card Authentication, which makes the authentication stronger because, to get access to Password Manager Pro, the user must possess the smart card and should know the personal identification number (PIN) as well.
Smart Card authentication in Password Manager Pro serves as the Primary Authentication and it should not be confused with the Two Factor Authentication.
If you have a smart card authentication system in your environment, you can configure Password Manager Pro to authenticate users with their smart cards, bypassing other first factor authentication methods like AD, LDAP or Local Authentication.
1. How Does the Authentication Mechanism Work in Password Manager Pro?
When the user attempts to access Password Manager Pro web-interface, he would be allowed to proceed further only if he had already completed the smart card authentication in the machine by presenting the smart card and subsequently entering the PIN. Password Manager Pro's web-interface supplements smart card technology with SSL communication. So, the user is prompted to specify their X.509 certificate for getting access.
The users can chose to provide the certificate from the smart card or the local certificate store, in which case Password Manager Pro performs the steps to authenticate the user with the certificate. The users can also choose to decline providing the certificate and Password Manager Pro takes them to the usual login page for authentication.
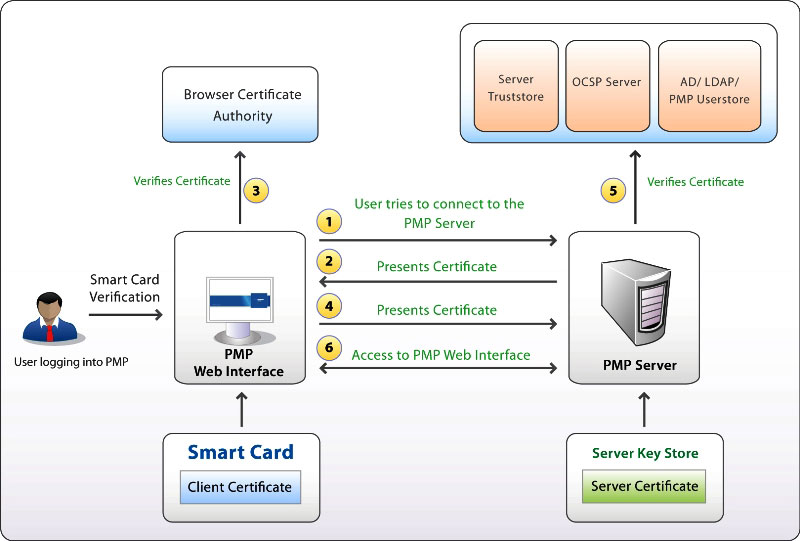
Smart card authentication workflow
- User tries to connect to the Password Manager Pro server.
- The Password Manager Pro server presents its certificate to the client (web-interface).
- The client verifies the server's certificate with that of the browser certificate authority.
- If the above process is successful, the client sends the user's smart card certificate to the server.
- The server verifies the client certificate with the server's trust store and then checks the revocation status with the OCSP server (if applicable); finally checks if the user certificate is same as the one in the AD/LDAP or Password Manager Pro user store.
- If the above process also succeeds, the Password Manager Pro server grants the user access to the web interface.
2. Enabling Smart Card Authentication
Summary of Steps
- Importing the root of the CA in case of internal certificates (your own certificate). This is the certificate authority issuing the X.509 user certificates to the Password Manager Pro users. If you are using a certificate signed by third-party CA, you may skip this step.
- Mapping user details between Smart card Certificate and the Password Manager Pro user store.
- Configuring status check for user certificates
- User certificates verification for authentication
- Enabling Smart Card Authentication in Password Manager Pro
- Restart Password Manager Pro Server & Web Browser
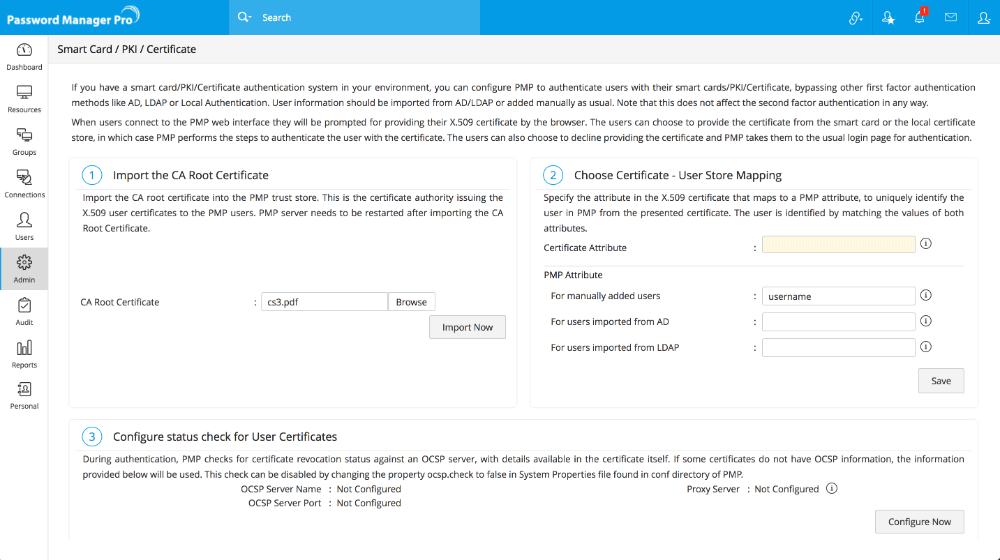
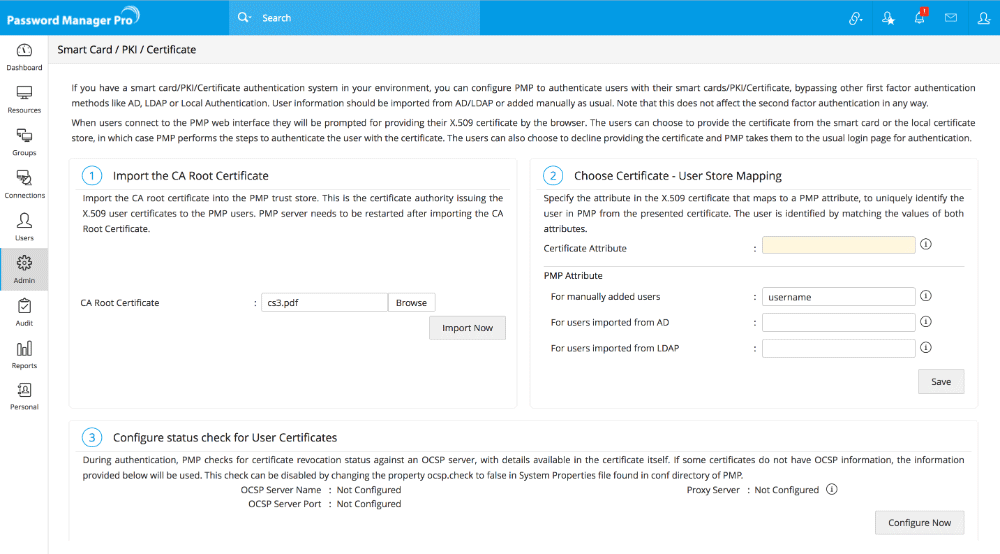
Step 1 - Importing the Root of CA
In case, you are using an already available internal certificate (your own certificate), you need to specify the root of the CA. If you are using a certificate signed by third-party CA, you may skip this step.
To import the root of the CA,
- Navigate to Admin >> Authentication >> Smart card / PKI / Certificate.
- In the UI that opens, click the Import Now button in Step 1.
- Specify the path of the root of the CA.
- Restart Password Manager Pro server.
Once you execute the above, the root of the CA will be recorded in Password Manager Pro. All the certificates signed by the particular CA will henceforth be automatically taken.
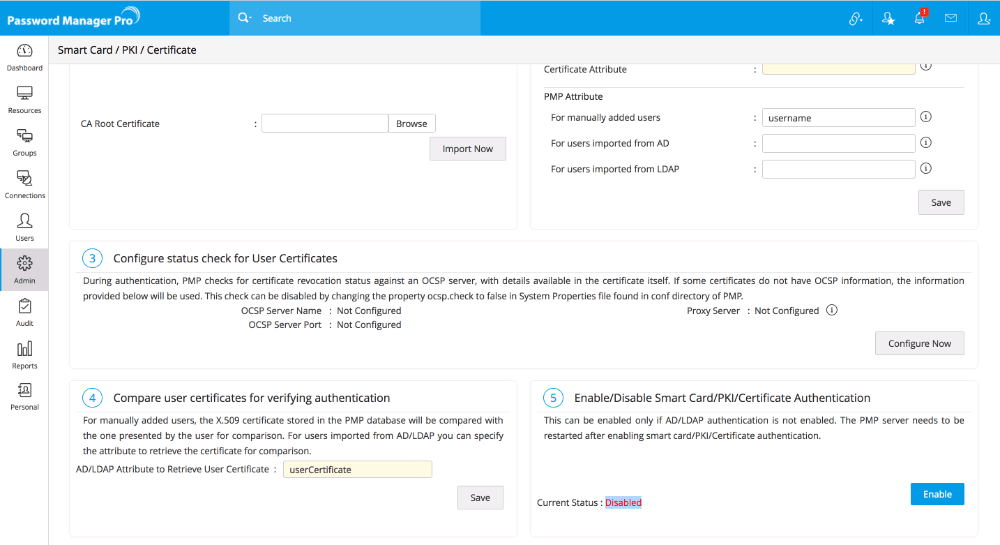
Step 2 - Mapping user details between smart card certificate and Password Manager Pro user store
The next step is to choose the mapping between the smart card certificate and the Password Manager Pro user database. That means, the attribute in the smart card certificate that uniquely identifies the user should match with the corresponding value in the Password Manager Pro user database.
This mapping involves two things:
- Specifying which attribute in certificate should be taken up for comparison.
- Specifying the corresponding matching attribute in Password Manager Pro user store.
Specifying the certificate attribute
- Password Manager Pro provides the flexibility to specify any attribute of the smart card certificate that you feel uniquely identifies the user in your environment. You may choose any attribute among SAN.OtherName, SAN.RFC822Name, SAN.DirName, SAN.DNSName, SAN.URI and Common Name. During authentication, Password Manager Pro reads the value corresponding to this attribute and compares it with the attribute in Password Manager Pro user store.
- From the drop-down Certificate Attribute, select the desired attribute.
Note: In case, in your environment, if any other attribute is used to uniquely identify the user, contact Password Manager Pro support to add that attribute.
Specifying the matching Password Manager Pro user name
After specifying the Certificate Attribute, you need to specify the mapping attribute in Password Manager Pro user store. That means, you need to specify the particular attribute that uniquely identifies the user in Password Manager Pro user store. This depends on how the user was added in Password Manager Pro - whether by manual addition or imported from Active Directory / LDAP.
Users manually added
For the users manually added into Password Manager Pro, username in Password Manager Pro is probably the only attribute that could be taken up for comparison with the corresponding attribute in certificate. So, just leave this text field with the default value "username".
Users imported from Active Directory / LDAP
- In the case of the users imported from Active Directory/LDAP, normally the attribute 'userPrincipalName' is used to uniquely identify the user. It is quite possible that in your environment, some other attribute like 'distinguishedName' might uniquely identify the user. So, specify the attribute accordingly.
- Finally, Save the settings.
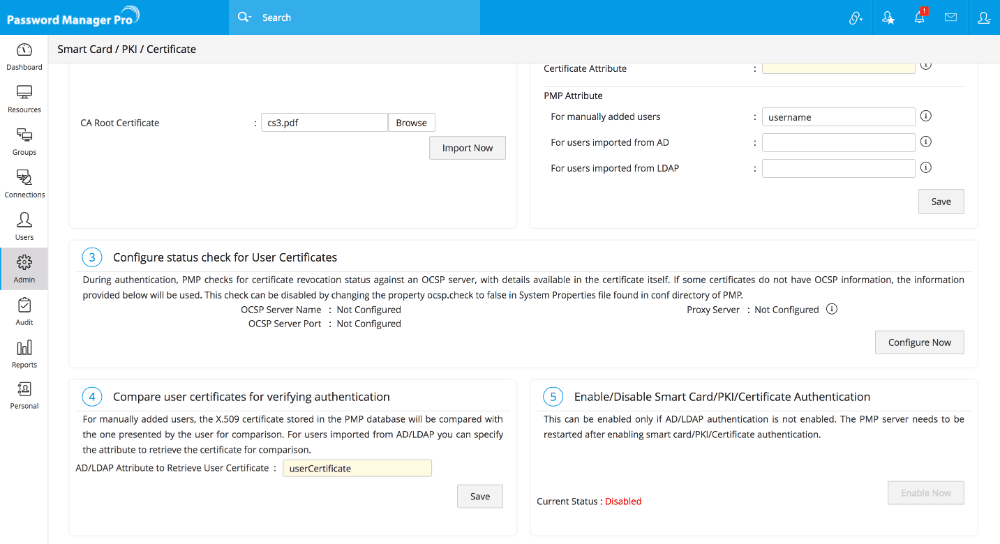
Step 3 - Configuring Status Check for User Certificates
During authentication, Password Manager Pro checks for certificate revocation status against an Online Certificate Status Protocol (OCSP) server, with details available in the certificate itself. If some certificates do not have OCSP information, the information provided in the settings here will be used. This check can be disabled by changing the property ocsp.check to false in 'System Properties' file found in conf directory of Password Manager Pro.
Also, authentication through OCSP will require access to the internet. In enterprise network setup, you might need to go through a proxy server to access the internet. You may specify proxy server settings if you have not specified it already.
- Click the button "Configure Now".
- In the pop-up form that opens, enter OCSP server details such as OCSP server name and server port.
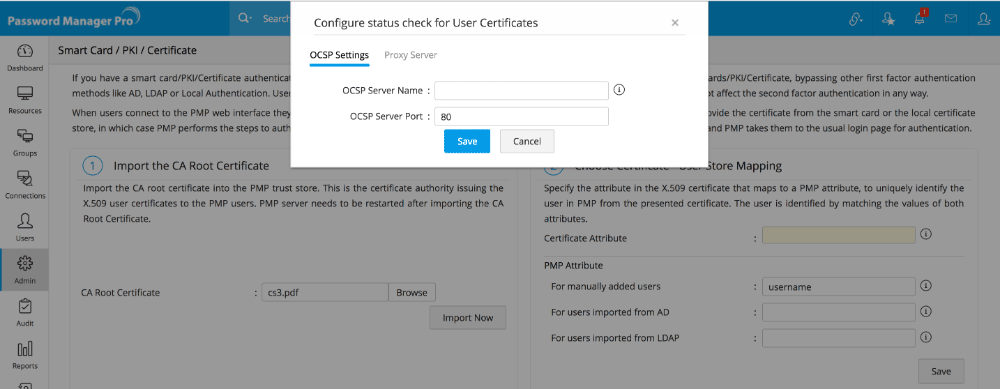
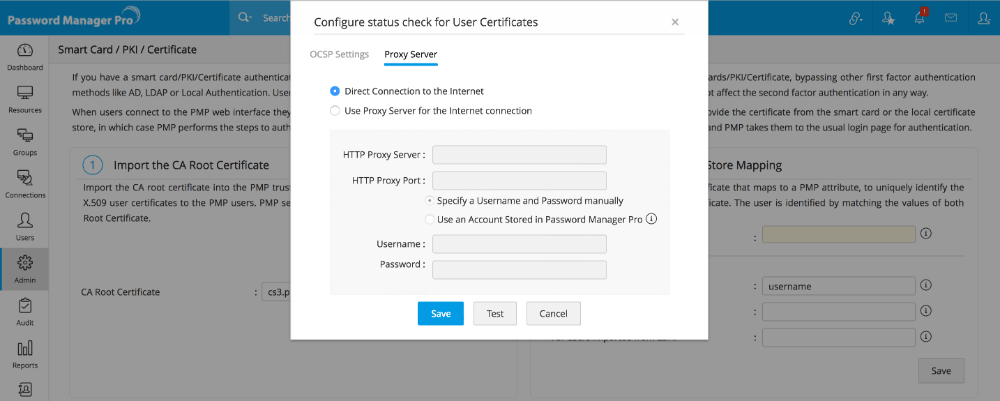
- Click "Save".
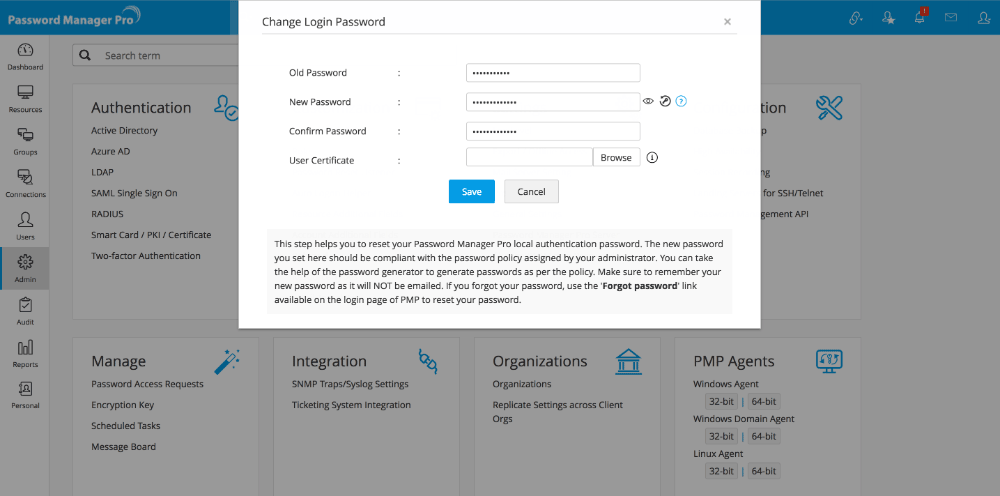
Step 4 - Comparing user certificates for verifying authentication.
Another step in the authentication process is comparison of the user certificates presented by the user and the ones stored in the system or Active Directory/LDAP. For the users who were added manually, the X.509 certificate stored in the Password Manager Pro database will be compared with the one presented by the user.
Note: In case, you do not have AD or LDAP in your environment, you need to manually put the x.509 format SSL certificate used for smart card authentication into Password Manager Pro.
- Navigate to Admin >> Settings >> Change PMP Login Password.

- In the pop-up form that opens, change the 'User Certificate' to specify the path of the x.509 format SSL certificate.
- Click "Save".
Step 5 - Enabling Smart Card Authentication
After carrying out the settings, you need to enable Smart Card Authentication. Before enabling this, you need to ensure that AD/LDAP authentication is disabled. Click "Enable" to enable smart card authentication.
Step 6 - Restart Password Manager Pro Server & Web Browser
After completing aforesaid steps, restart Password Manager Pro server and the web server once to give effect to the settings. Whenever you enable or disable Smart Card authentication in Password Manager Pro, you need to restart the server and the browser to give effect to the change.
Important Note:
- Once you enable smart card authentication, it will take effect globally - that means, Smart card authentication will be applied to all the users. However, the users for whom smart card authentication is not applicable, will be prompted to use local authentication automatically.
- When smart card authentication is enabled, AD or LDAP authentication will remain suspended for all users. So, you need to choose between AD, LDAP and Smart card.
3. Smart Card Authentication in Password Manager Pro - Workflow
- User tries to access Password Manager Pro web-interface.
- The attribute that uniquely identifies the user in the smart card certificate is compared with the corresponding attribute in Password Manager Pro userstore.
- Then, the user certificate - the X.509 certificate stored in the Password Manager Pro database in the case of users manually added will be compared with the one presented by the user. In the case of users imported from Active Directory / LDAP, the certificate will be retrieved from AD/LDAP for comparison.
- If there is perfect matching, user is allowed access.
4. Smart Card Authentication in High Availability Scenario
If you have configured high availability and if you have enabled smart card authentication in Primary, the same has to be configured in the secondary server too.
To do this,
- Stop the Password Manager Pro primary server.
- Connect to the Password Manager Pro secondary server.
- Go to Admin >> Authentication >> Smart card / PKI / Certificate.
- In the UI that opens, perform Step 1 and Step 5 alone (for details, refer to the section 'enabling smart card authentication' above).
- Restart secondary after completing the above steps.
Troubleshooting Tip
- In case, you do not get the pop-up that prompts you to select the client certificate during authentication, try again after restarting the browser